Chrome Extension for gpg in Gmail
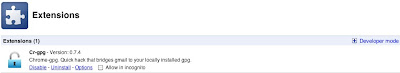
Last month we released an alpha version of cr-gpg . This is a simple Chrome extension to enable gpg functionality in gmail (or Apps for Domains). (If you don't know what gpg is, you should first read this and this .) Installation : You can grab the extension from [ here ] and a double click should install it , after the install is completed you should see the image above if you navigate to chrome://extensions : Options : Once you have installed the plugin, there are 2 required configuration options: 1) Directory with gpg binary 2) Temp folder path (writable by the browser) (cr-gpg simply calls out to the gpg installation on your machine. Option [1] therefore is asking where it can find the gpg executable, and Option [2] is looking for a scratch directory to do its work). (We make some effort to ensure that the temp directory is well maintained). You should be able to click "Use Default" on most installations. The "Encrypt to self" option is fairly self explana...